
One of the highest-impact Windows vulnerabilities patched this year is now under active exploitation by malicious hackers, Microsoft warned overnight, in a development that puts increasing pressure on laggards to update now.
CVE-2020-1472, as the vulnerability is tracked, allows hackers to instantly take control of the Active Directory, a Windows server resource that acts as an all-powerful gatekeeper for all machines connected to a network. Researchers have dubbed the vulnerability Zerologon, because it allows attackers with only minimal access to a vulnerable network to login to the Active Directory by sending a string of zeros in messages that use the Netlogon protocol.
Zerologon carries a critical severity rating from Microsoft as well as a maximum of 10 under the Common Vulnerability Scoring System. Despite the high rating, the escalation-of-privileges vulnerability received scant, if any, attention when Microsoft patched it in August, and Microsoft deemed the chances of actual exploitation “less likely.”
The security world finally took notice last week with the release of several proof-of-concept exploits and a detailed writeup, which demonstrated severity of the vulnerability and the relative ease in exploiting it.
All hands on deck
On Wednesday evening, Microsoft issued a series of tweets that Zerologon was now being exploited in the wild.
“Microsoft is actively tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon,” Microsoft representatives wrote. “We have observed attacks where public exploits have been incorporated into attacker playbooks.”
Microsoft 365 customers can refer to the threat analytics report we published in Microsoft Defender Security Center. The threat analytics report contains technical details, mitigations, and detection details designed to empower SecOps to detect and mitigate this threat.
— Microsoft Security Intelligence (@MsftSecIntel) September 24, 2020
The company provided several digital signatures of files used in the attacks, but it didn’t publicly provide additional details. Microsoft has published a threat analytics report that’s designed to help administrators assess the vulnerability of their networks, but it’s available only to Office 365 subscribers. For everyone else, the best resource is this white paper from Secura, the security firm that discovered Zerologon. Microsoft representatives didn’t respond to an email asking for a copy of the analytics report.
Crown jewels
It’s hard to overstate the severity of an exploit that makes it possible to take control of an Active Directory using several dozen lines of code. Active Directories (and the domain controller servers they run on) are the resources most cherished by ransomware attackers. With control over the central provisioning directory, they can infect entire fleets of machines within minutes. Nation-sponsored hackers performing surgical-precision espionage campaigns also prize such access because it allows them to control specific network resources of interest.
Both types of attackers often begin hacks by compromising a computer with low-level privileges on a network, often by tricking an employee into clicking on a malicious link or file or by entering a password on a phishing page. It can sometimes take weeks or months to escalate low-level privileges to those needed to install malware or execute commands. In certain cases, Zerologon can allow an attacker with this kind of toehold to almost instantly gain control of the Active Directory.
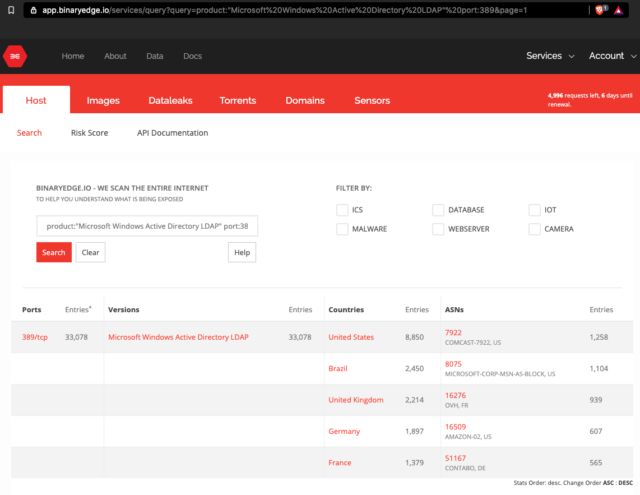
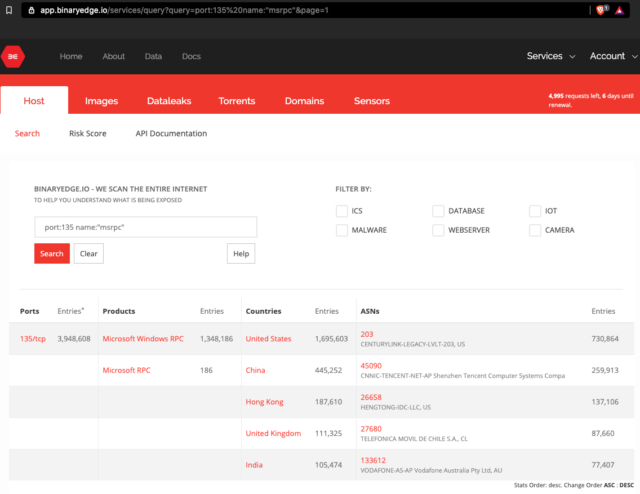
There may also be ways to exploit Zerologon directly from the Internet with no previous access. Internet searches like this one and this one show more than 33,000 and 3 million networks are exposing domain controllers and Remote Procedure Call login servers to the public Internet. In the event a single network is exposing both resources, the combination may leave a network wide open with no other requirements.
The risk posed by Zerologon isn’t just that of facing a catastrophic hack. There’s also the threat of applying a patch that breaks a network’s most sensitive resource. Late last week, the cybersecurity arm of the Department of Homeland Security mandated agencies to either apply the patch by Monday night or remove domain controllers from the Internet.
With word less than three days later that exploits are in the wild, it’s clear there was good reason for the directive.