An adware family known primarily for distributing browser hijackers has been caught distributing full-blown malware, security researchers said today in a talk at the VirusBulletin 2020 security conference.
“What’s dangerous about Linkury is how it uses its adware front as a gateway to propagate malware,” said Arun Kumar Shunmuga Sundaram & Rajeshkumar Ravichandran, two malware analysts at Indian security firm K7 Computing.
“It walks a very fine line between typical adware and malware, and we have seen how it can switch sides based on geolocale,” the two said.
“It has tailored its operations to cloak its malicious techniques and flies under the guise of ‘legitimate, law abiding’ adware, giving it recourse to plausible deniability of any wrongdoing.”
While cyber-security companies like Malwarebytes, Microsoft, or Trend Micro are currently detecting Linkury operations as “adware,” Sundaram and Ravichandran argue that “the case for flagging it as malware is strong based on the evidence presented in [their] paper.”
What’s Linkury?
Prior to K7’s VirusBulletin presentation today, Linkury was primarily known as an adware operation.
Its main method of distribution is the SafeFinder widget, a browser extension ironically advertised as a way to perform safe searches on the internet.
The widget is usually bundled with other free apps as a secondary installer or is distributed via online ads that redirect internet users to SafeWidget download pages.
Installing the SafeFinder extension would usually changes a user’s default browser search and home tab settings but also install additional binaries, different based on the user’s country.
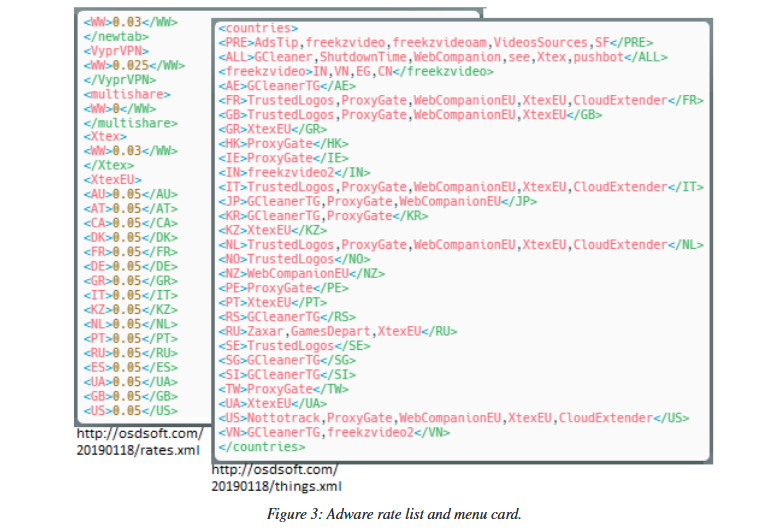
In most cases, these binaries would be other apps, for which developers paid a fee to be included in the SafeFinder installation process.
But K7 researchers say that in recent cases they analyzed, the SafeFinder widget has now also begun installing full-blown legitimate malware, such as the Socelars and Kpot infostealer trojans.


In other cases, the Linkury operation also dropped a version of the Opera browser on infected hosts, which they started silently in the operating system’s background to deliver pop-up ads and generate profit for the Linkury operators.
But the Linkury team also used the SafeFinder widget to force-install extensions on the user’s browsers. K7 reported Linkury force-installing extensions in Chrome and Firefox, for Windows users; and Safari, Chrome, and Firefox, for Mac users.
Furthermore, K7 researchers also noted that the SafeFinder installer also contained many features specific to malware, such as PowerShell scripts to disable Windows Defender, and functions to detect when the installer was executed inside virtual machines and sandboxes, environments usually used for malware analysis — which it obviously wanted to avoid.
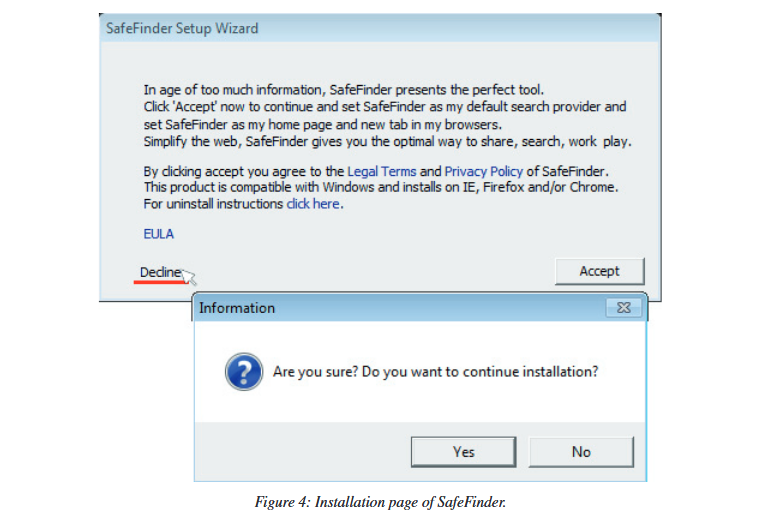
And last but not least, Linkury’s SafeFinder widget had no intention of honoring user choices, with its installer specifically designed to install its payload even if the user tried to avoid the installation process, like pressing “No” as in the image below.